Using a Custom or Private CA
To enable your enable your Gitpod Dedicated instance to use certificates signed by a custom or private Certificate Authority, you will need to follow the process below. For more information about how to create a Gitpod Dedicated instance, please see Getting Started.
ℹ️ Adding a custom CA can also be done once an instance is already running. However, this requires coordination with Gitpod, as Gitpod needs to ship a new release to the instance that updates the internally used domain.
The process to use custom domains requires:
Upload the custom CAs certificate needs to AWS secret Manager.
How to upload the CA certificate to AWS Secret Manager in the same AWS account that the Gitpod instance runs in.
- In the AWS account that the Gitpod instance runs in, navigate to the Secret Manager within the AWS Console. Click on Store a new secret. Select the Secret Type as Other and input your certificate in plain text as illustrated below
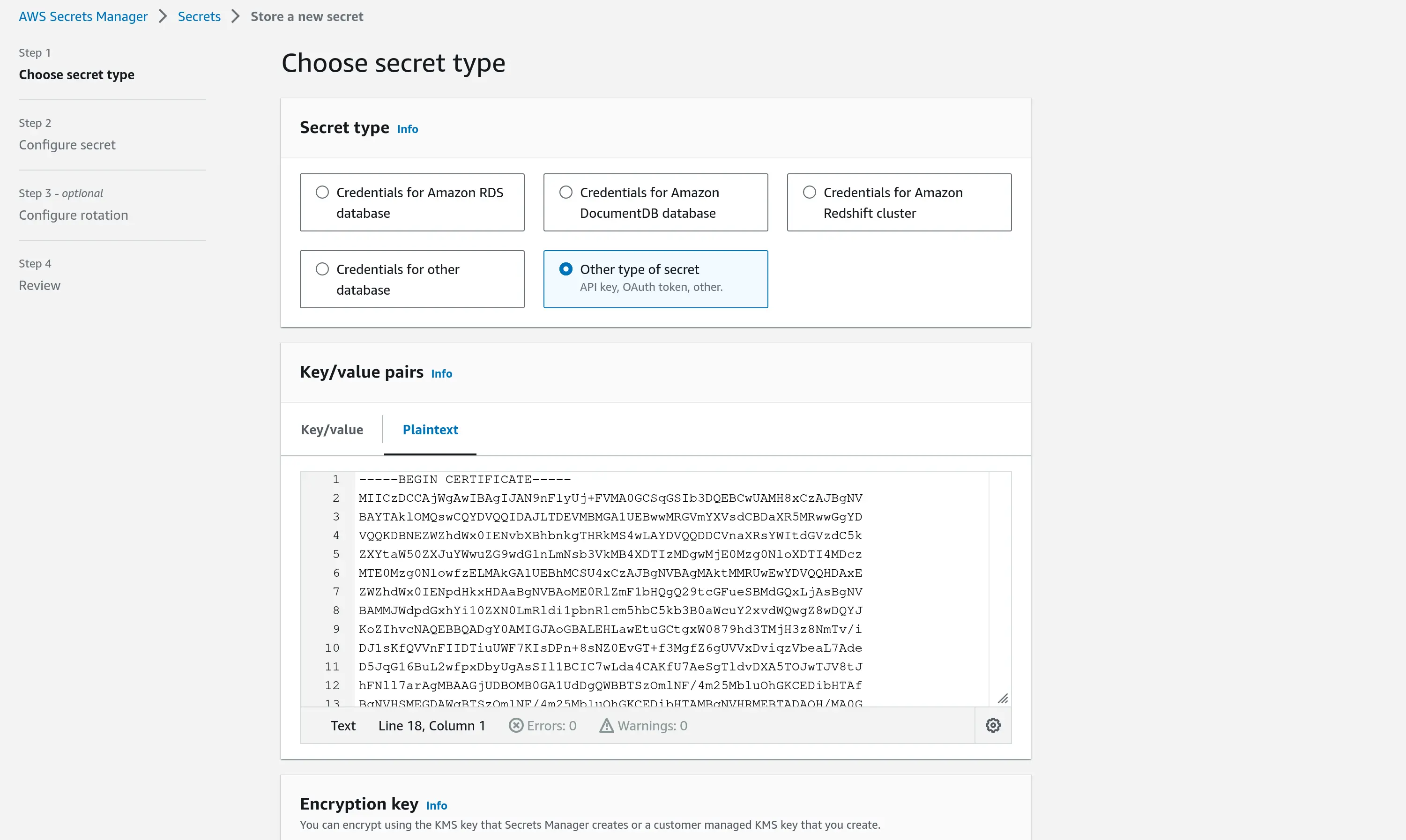
- You can either choose to use the default KMS Encryption Key or create a new one
- Follow the instructions on screen and store the secret
- Note down the ARN of the secret
How to upload the CA certificate to AWS Secret Manager to another AWS account and make it accessible to the Gitpod instance’s AWS account
In the preferred AWS account, navigate to the Secret Manager within the AWS Console. Click on Store a new secret. Select the Secret Type as Other and input your certificate in plain text as illustrated below
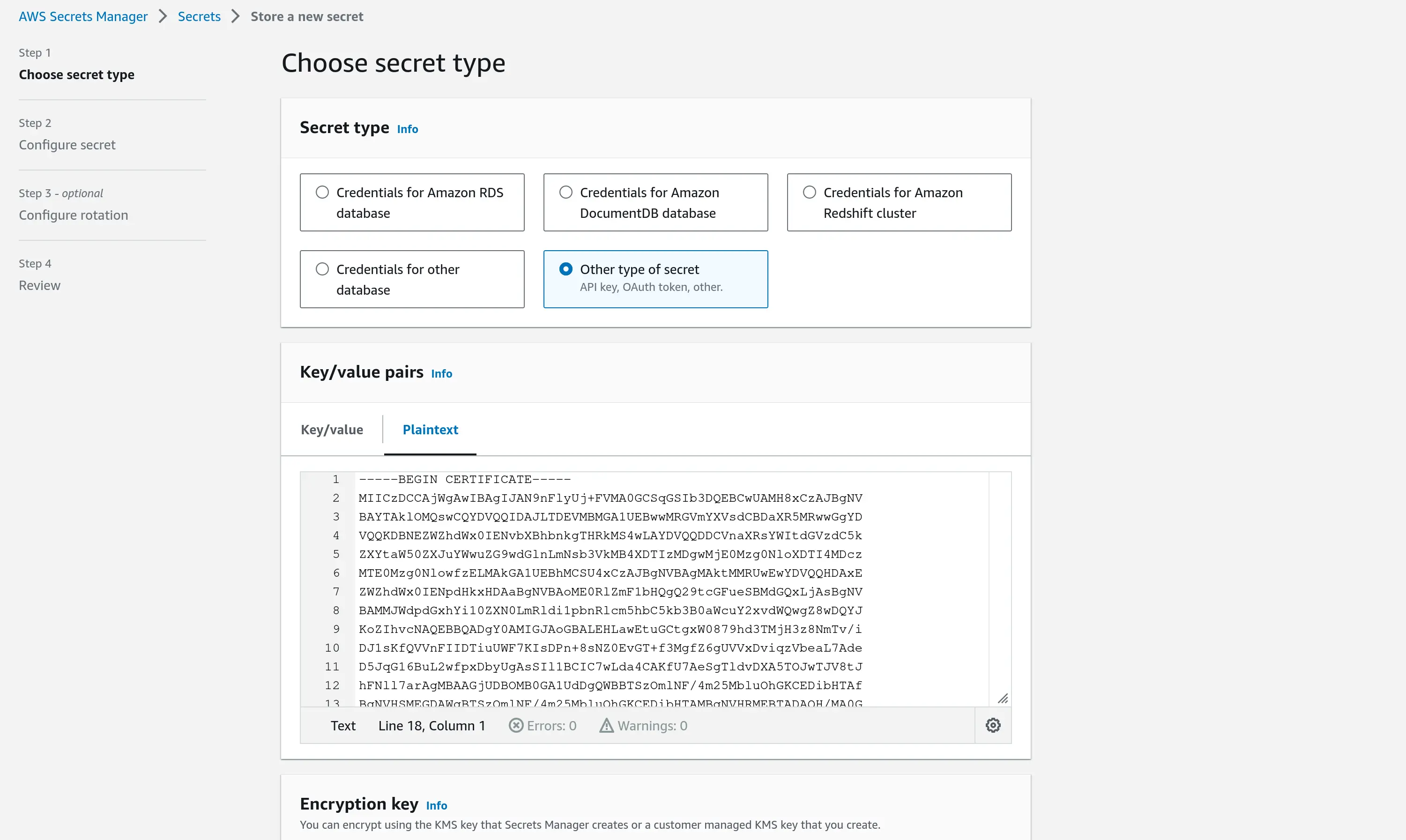
Create or choose a different KMS Encryption key than the default
aws/secretmanagerkey. This is very important because secrets signed with the default key cannot be shared with other accounts. When creating the key, allow access to the Gitpod instance’s AWS account to the key by providing the account ID as can be seen in the image: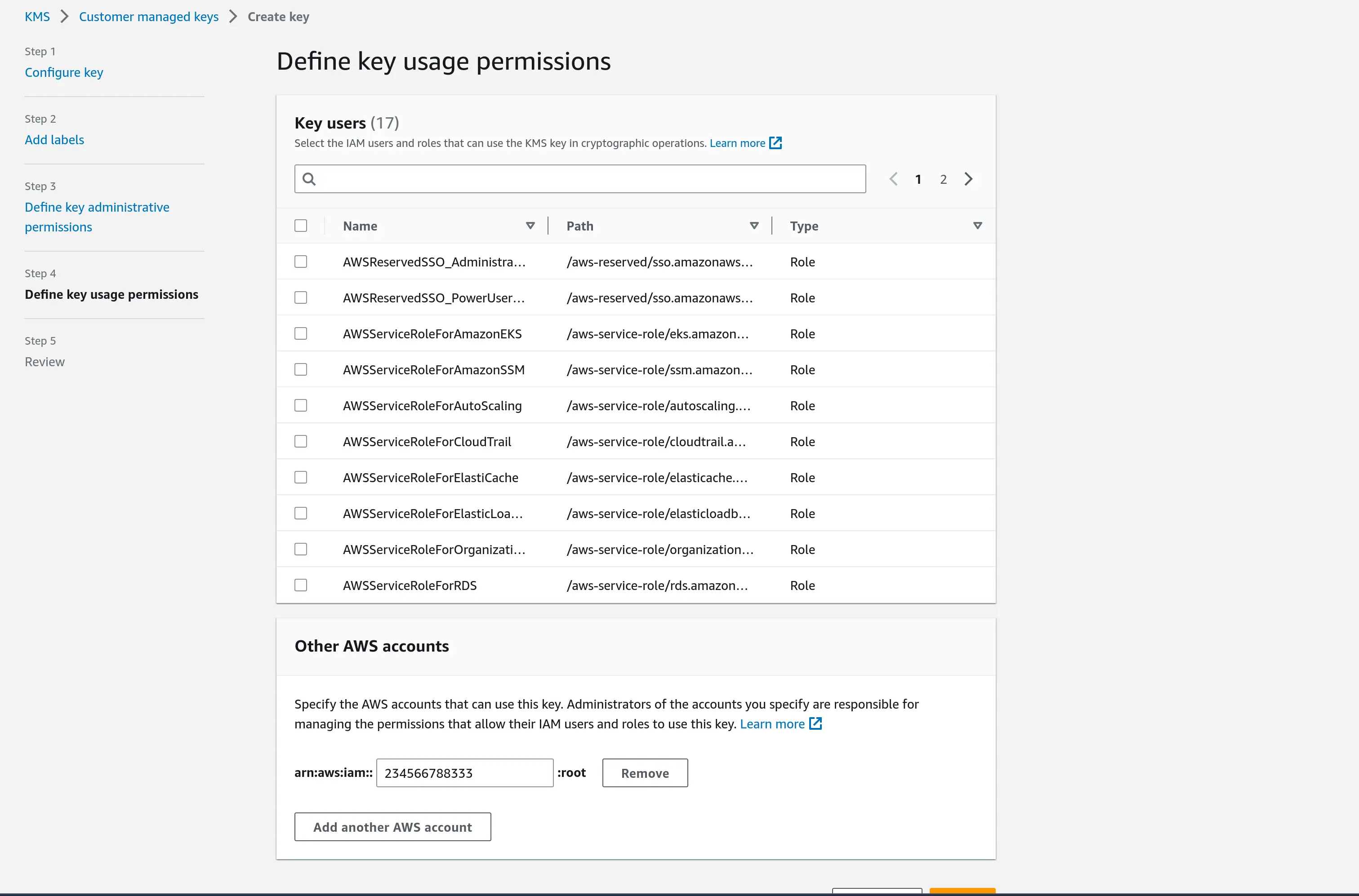
- If you are using a pre-existing encryption key, you should add a policy like this:json
language:
{ "Sid": "Allow use of the key", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::<gitpod-instance-aws-id>:root" }, "Action": [ "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "<* OR ARN of key>" }
- If you are using a pre-existing encryption key, you should add a policy like this:
Store the secret following the instructions
Once the secret is created, edit the permissions of the secret and allow access from the cell AWS account (secret-arn is the arn of secret that was just created)
jsonlanguage:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::<gitpod-instance-aws-id>:root" }, "Action": "secretsmanager:GetSecretValue", "Resource": "<secret-arn>" } ] }Note down the ARN of the secret.
- In the AWS account that the Gitpod instance runs in, navigate to the Secret Manager within the AWS Console. Click on Store a new secret. Select the Secret Type as Other and input your certificate in plain text as illustrated below
Provide the
ARN of the certificateto your Gitpod Account Manager. The certificate needs to be accessible to the account where Gitpod is installed in.Create the instance as per Getting Started.
Domains signed by the custom CA should now be accessible.