TLS configuration for Gitpod Self-Hosted
⚠️ Gitpod Self-hosted has been replaced with Gitpod Dedicated, a self-hosted, single-tenant managed service that runs in your private cloud account but is managed by us.
Try out Gitpod Dedicated.
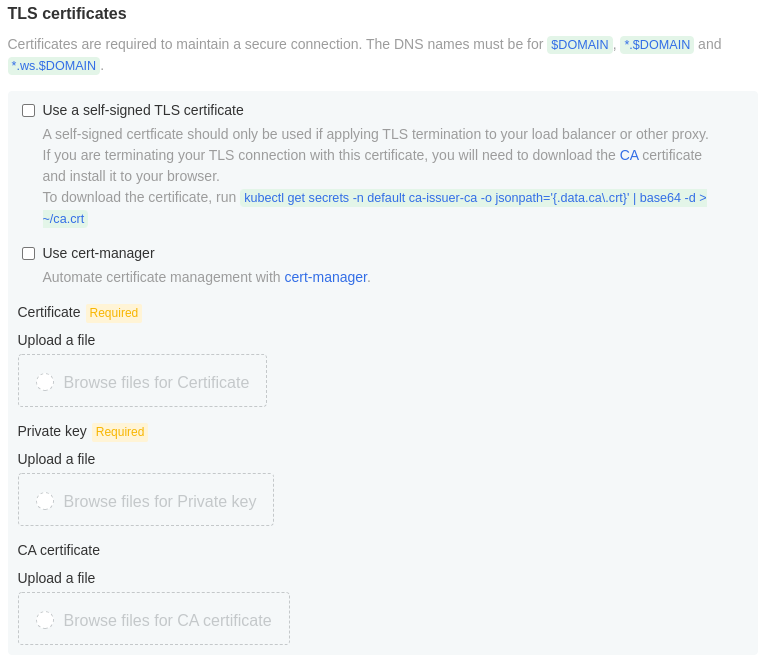
To run your own Gitpod instance, you need a TLS certificate for your Gitpod domain. There are three options to provide these TLS certificates.
Option 1: Cert-Manager
Configure cert-manager to issue these certificates (usually with a DNS-01 challenge and services like Let’s encrypt). See the installation guide) for more information.
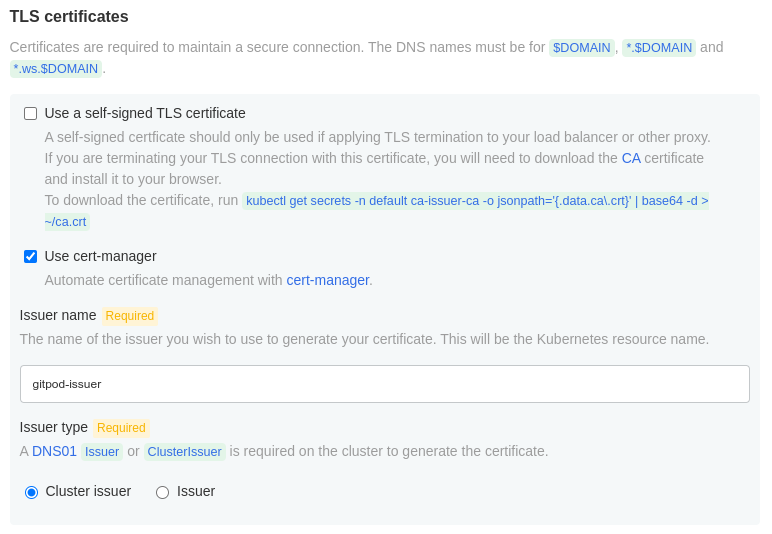
TLS certificates configuration options during the installation process
Option 2: Self-signed by Gitpod
We usually do not recommend this option for production usage.
Let Gitpod generate self-signed certificates for your installation. This option can be used in case your load balancer does the TLS termination or for testing settings. For the latter case, you need to add the custom CA to your browser to let it accept the self-signed certificate. Use this command to export the CA:
$ kubectl get secrets -n ca-issuer-ca -o jsonpath='{.data.ca\.crt}' | base64 -d > ~/ca.crt 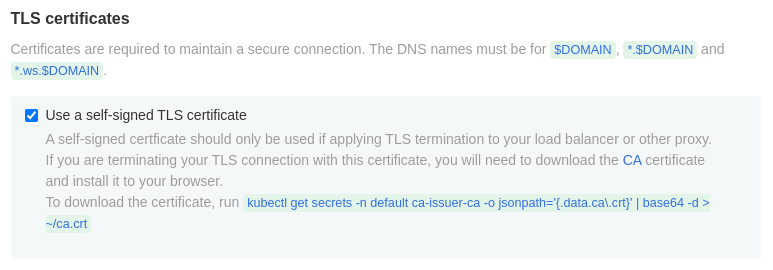
Option 3: Bring your own certificate
⚠️ Limitation
Adding custom CA certificates is currently not supported on Google Kubernetes Engine (GKE) because on GKE
containerddoes not support custom certificates.
Upload your own TLS certificate, key, and (optionally) CA certificate. When your TLS certificate is signed by a publicly accepted TLS authority, you just need to upload your certificate and key. In case it is a self-signed certificate (e.g. signed by a corporate CA), you also need to upload your CA.